THE ARCHITECTURE OF FOGNIGMA
Three Layers of
Quantum-resistant Encryption
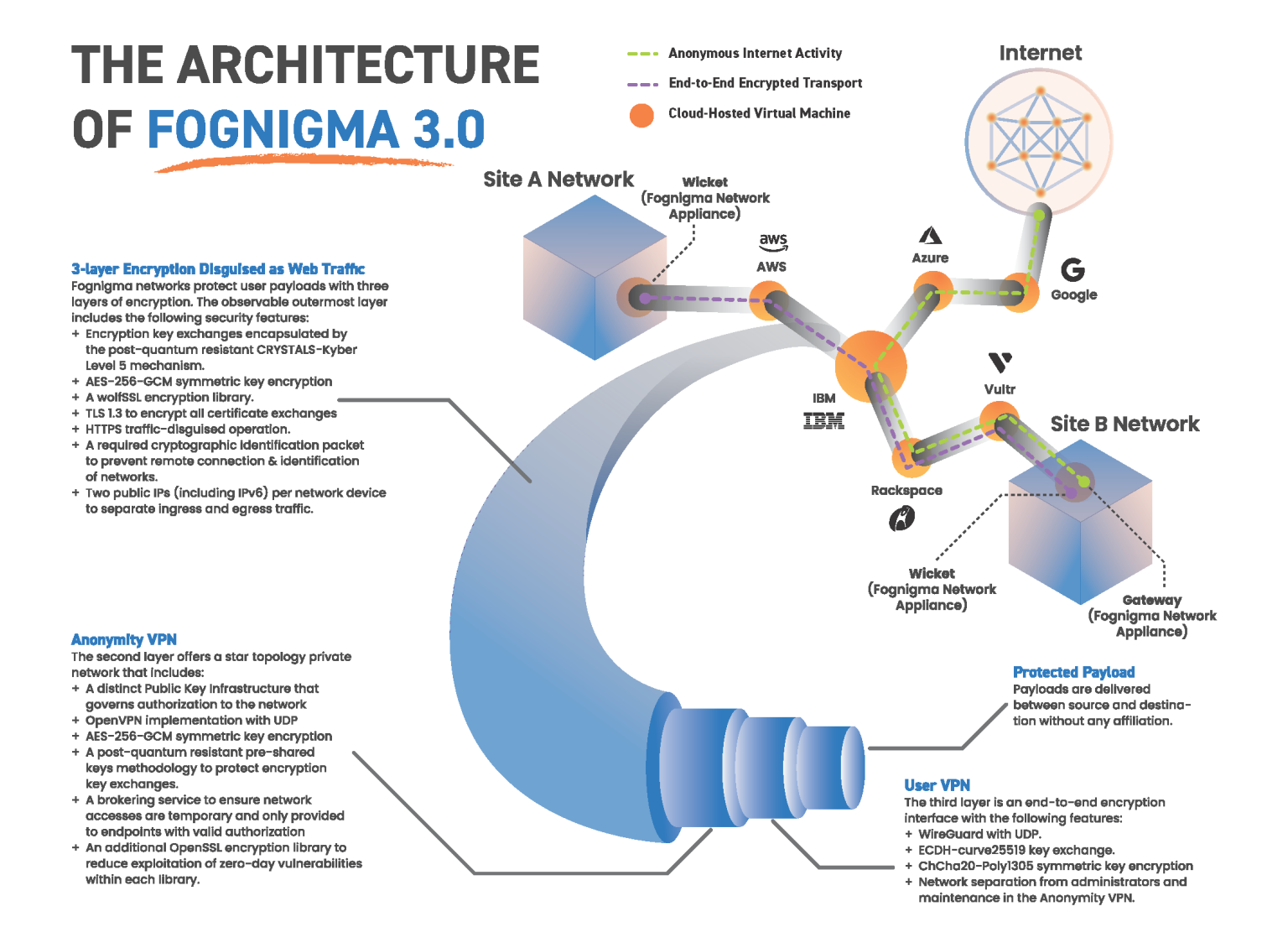
Fognigma is designed with a unique, three-layer encryption architecture that protects data during transfer, uses multiple encryption libraries, and incorporates quantum-resistance—all while disguising protection as typical web traffic.
FOGNIGMA ENVIRONMENTS
Zero Trust. Least Privilege. Quantum Resistance.
Fognigma's encryption architecture incorporates Zero Trust, least privilege, and quantum-resistance, so every environment is built the right way, minimizing every potential risk and exploit from the ground up.
Smart Firewall
The outermost encryption layer incorporates ZeroProfile, Fognigma’s smart firewall that makes networks invisible to port scans and other attacks.
Multiple Libraries & Keys
Different encryption libraries and key mechanisms are incorporated throughout each layer to prevent zero-day exploits.
Quantum Resistance
Quantum resistance is provided by the outermost encryption layer's CRYSTALS-Kyber Level 5-encrypted key exchanges and the middle layer's pre-shared keys methodology.
Traffic Splitting
Ingress and egress traffic is split by two public IPs (IPv4 & IPv6) per network device.
Least Privilege
A dedicated brokering service ensures that all network accesses are temporary and only provided to endpoints with valid authorization.
Zero Trust
The innermost layer provides network separation from administrators and maintenance in the middle layer, protecting against insider attacks.
LEARN MORE ABOUT HOW
Fognigma Commands The Cloud
Fognigma is much more than its unique architecture and design. Learn more about our innovative networking, application, communication, and security solutions.
Network Solutions
Rapidly deploy invisible digital environments, anonymize activity and connections, and more, from headquarters or anywhere:

Application Solutions
Anonymously access virtual desktops and mobile environments, automatically encrypt messages and files, view live GPS data without delay, and more with Fognigma's suite of specialized applications:

Communication Solutions
Communicate with encrypted voice, video, text, and more anywhere and from any device—no software installation needed:

Security Solutions
Protect your environments, operations, users, and data, from the moment Fognigma is deployed to after an operation is complete:
FOGNIGMA
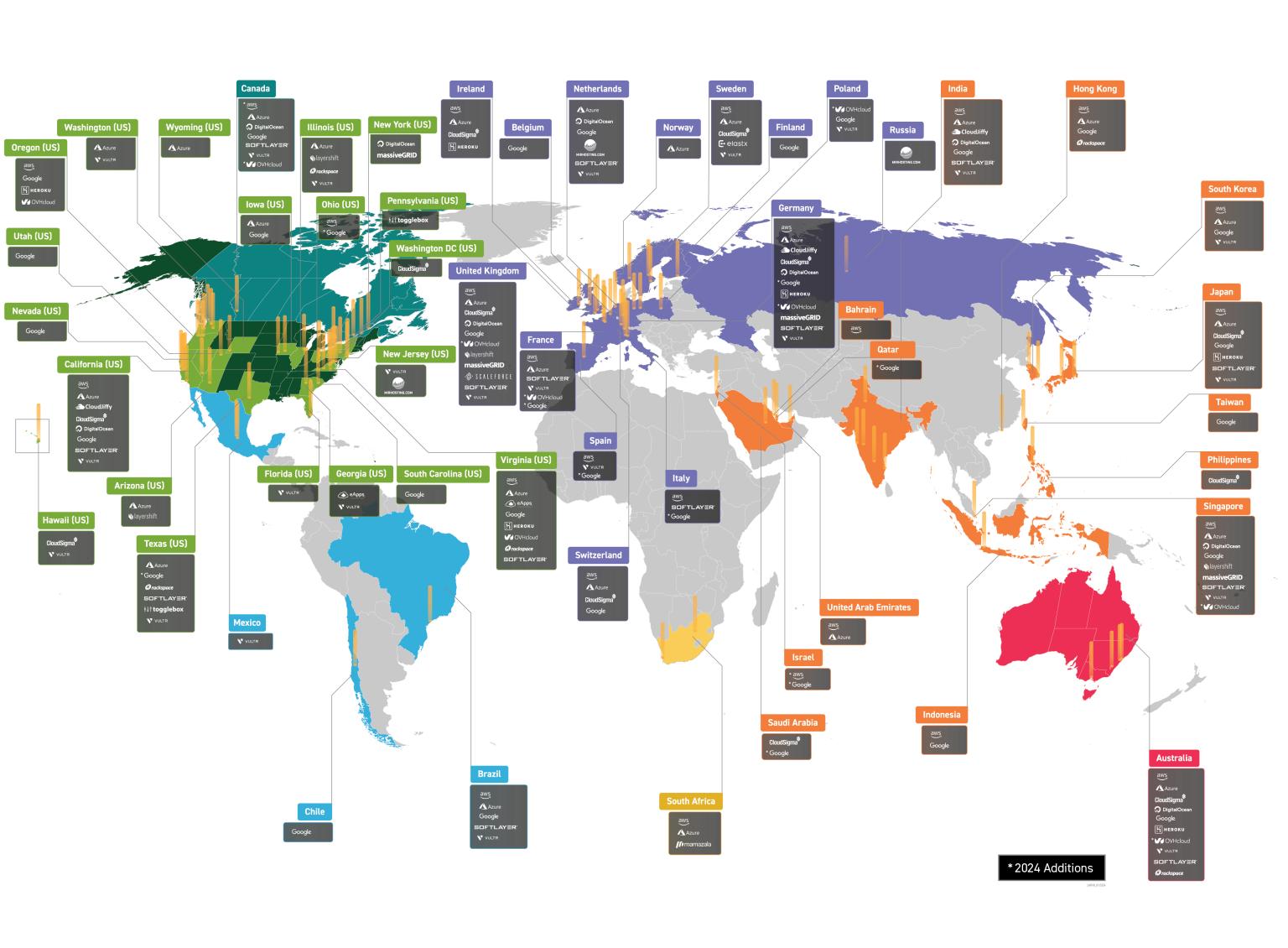
Global Protection. Global Reach.
Ensure the success of your operations, no matter where you are—or where you want to appear to be.