VIRTUALIZED ANDROID ENVIRONMENTS
Anonymous Cloud-hosted Android Instances
Securely access virtualized Android instances from any device to access mobile apps and custom software, browse the web anonymously, and instantly share files between other Virtual Android users in the same network.
BYOD
Virtual Androids work with any desktop or smartphone, including those using non-Android operating systems.
File Transfers
Virtual Androids allow users to easily transfer files between an instance and the device accessing it.
Anonymous Access
Every instance is automatically deployed with a proxy for anonymous access. Audio transmitted through Virtual Androids is filtered through proxies to ensure no IP leaks occur.
Automation
Fognigma automatically deploys and maintains instances so they’re always available when needed. When a user reserves an instance, Fognigma automatically deploys a new one to replace it.
Anonymously Access Virtualized Mobile Environments From Any Device, Anywhere
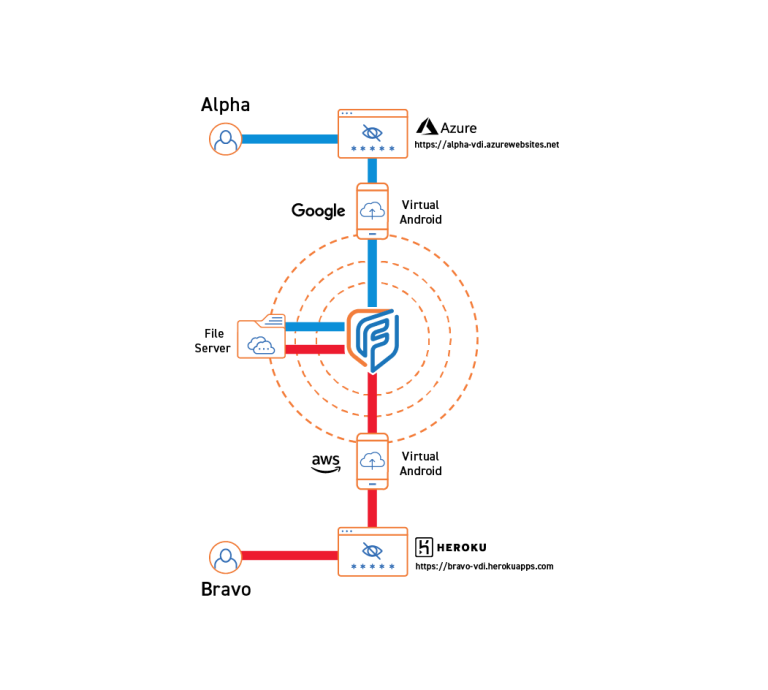
Fognigma’s Virtual Androids are sandboxed, single-use, disposable mobile environments that allow users to access mobile applications and resources within a Fognigma Network or the public internet via a protected, traceless connection. Virtual Androids drastically reduce the risks of IP association, malware, and attack when compared to standard mobile devices.

VIRTUAL ANDROIDS IN ACTION
Scenario: Covert Mobile Application Access & Anonymous Research
Operatives from an organization are conducting local research in an area under heavy surveillance. They require access to specialized mobile applications without having to install them on their existing mobile devices, and they cannot be associated to each other or their organization. To provide access, a Fognigma administrator can deploy Virtual Androids and install the software there.
From the FOGNIGMA interface, the administrator deploys several Virtual Androids with the applications needed for the mission.
The administrator shares a unique URL with each user, which Fognigma generates automatically for each Virtual Android instance, to provide secure and anonymous access.
Users sign into the Virtual Androids with their credentials and immediately gain access to the applications. Any data collected can be shared amongst operatives through the Virtual Android instances.
At the end of the users’ sessions, the Virtual Androids are automatically destroyed without leaving digital forensics.