REMOTE ACCESS TO PRIVATE RESOURCES
Fognigma's Remote LAN Access
Access LAN Resources and Devices Remotely
Remote Access
Netcutters connect to a Fognigma VPN and appear as an Exit Point. If they are installed in a remote, secure network, authorized users can access the private resources on that remote network as long as they are connected to the Netcutter’s Exit Point.
Exit Points Anywhere
Since Netcutter can connect to two networks simultaneously, one to communicate with a Fognigma VPN and one to direct network traffic from inside the VPN, a Netcutter can create a Fognigma Exit point anywhere in the world.
VDI Integration
Netcutters are fully compatible with Fognigma-protected VDIs. With the pre-installed Exit Switcher application, VDI users can select the Netcutter Exit Point to monitor private resources remotely or appear to be using the Internet from the Netcutter's location.
Cellular Integration
Users with 3G/4G cellular service can connect a Netcutter to a mobile phone to generate an Exit Point from the mobile phone's network. Once connected, their web traffic will appear to be originating from that cellular network and location.
Protect Isolated Resources
& Provide Access To Them
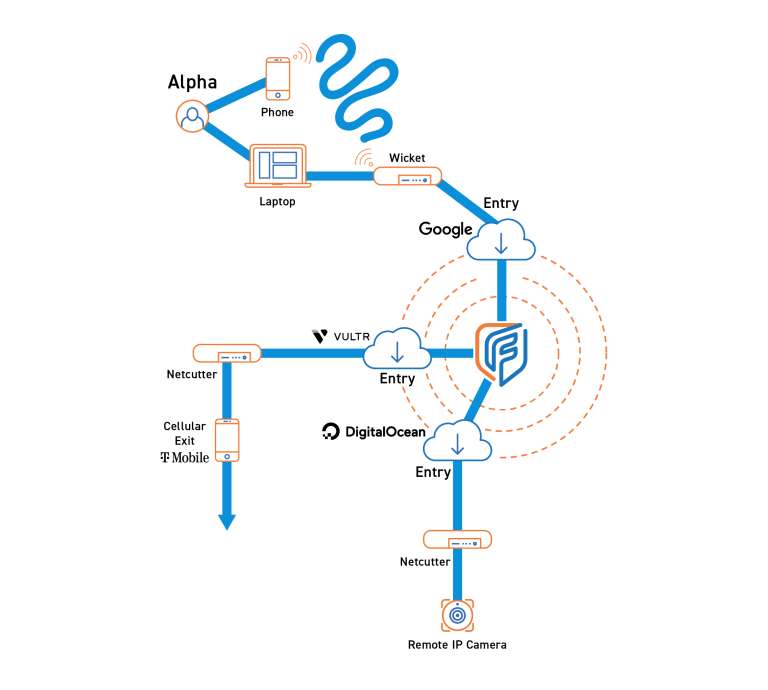
A Netcutter is a hardware device that creates an exit point within a Fognigma Network. When connected to a LAN, a Netcutter allows Fognigma users to access the LAN and any LAN devices from anywhere in the world. Once connected, users’ connections appear to be generating from the Netcutter location, allowing users to remotely monitor LAN devices, such as office security cameras, while maintaining the appearance that they are at the office.
NETCUTTER IN ACTION
Scenario
An organization based in Northern California has a remote facility located in Southern California, hours away from their headquarters office. Rather than dedicating staff and hours to monitor cameras and network security by physically going to their other facility, administrators create a firewall for the network to block all inbound traffic. To remotely monitor the facility and all sensitive
remote equipment, they connect a Netcutter to the remote facility’s network and configure a whitelist so authorized users can connect to a Fogngima Network to access the Netcutter and LAN resources.
The systems administrators enter their Fognigma credentials to connect to the engine.
The administrators select the network dedicated to the remote facility and select the exit generated by the Netcutter.
The administrators connect to the LAN and monitor the network and devices remotely, while generating traffic from the remote facility’s location